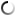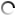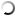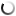How Does IoT Data Collection Work?
The Internet of Things is making its way into every facet of our daily lives — the vehicles we drive, the cities we live in, the way we shop, how we take care of ourselves, etc. Although all the opportunities this innovation offers are yet to be explored, business owners and public offices can already benefit from gathering more data about customers and community residents than ever.
There’s a lot of power in being able to collect and process insights in real-time. However, with great power comes great responsibility, and tech teams need to approach data collection and management responsibly, designing reliable and secure application architectures. In this post, we’ll examine the steps of IoT sensor data collection, analyze the overall architecture of an Internet-of-Things-based project, and go over the challenges project managers need to account for.

Table of Contents
- Types of IoT Sensor Data
- What Industries Benefit From Data Collection Technology
- Importance of Data Collection in the IoT Environment
- Data Security in IoT
- Challenges in IoT Data Collection
- Data Collection Solution at Digiteum
Types of IoT Sensor Data
Broadly speaking, IoT data is the information collected by connected devices — sensors, wearables, and others. However, not all types of sensor data are equally complex. Here is the breakdown of the main insight categories a tech team can collect — from the most basic to the most advanced.
Status data
Status data is the baseline for most IoT applications. It’s the most basic type of information gathered — whether an appliance is off or on, whether there are available spots at a property, etc. This data is useful for all decision-making, planning, and maintenance. However, it may have little value if not paired with other types of IoT data.
Location data
Tracking the movement of an object or a person is another important function of IoT devices and sensors. Connected systems use location data for fleet management, asset tracking, employee monitoring, and other management tasks. IoT may offer higher data processing speed and precision than GPS — that’s why a lot of business owners and public office managers use motion sensors instead of GPS trackers.

Automation data
This type of data helps IoT systems control devices inside a house, vehicles on the road, and other moving parts of any system. Processing automation data is a complex process since the stakes in case of errors are extremely high — from accidental lockdown to traffic accidents. Having said that, once security practices and a code of conduct are established, an increasing number of IoT systems will rely on automation data. Teams will be able to allocate human resources efficiently and encourage talent to focus on carrying out demanding assignments, not routine tasks.
Actionable data
These types of IoT datasets are an extension of status data. Other than capturing bare insight, the system processes it and transforms into easy-to-carry-out instructions. Actionable data is often used in forecasting and prediction, energy consumption and workplace efficiency optimization, as well as during long-term decision-making. Through actionable data, business owners and public officials can make better use of other insights an IoT system has captured.
What Industries Benefit From Data Collection Technology
The Internet of Things is still an emergent technology — it’s too early to narrow its applications down to several industries. However, as far as IoT implementation goes, the following fields are among the frontrunners in deploying connected devices and making the most out of Internet of Things and big data collection:
- Healthcare. From personal monitoring devices to hospital tracking systems, connected devices caregivers and caretakers use rely on sensor data. The ability to monitor patients in real-time helps healthcare professionals improve the precision of diagnosis, as well as the speed of post-op recovery. Other than that, IoT devices help ensure safety inside the facility, tracking both patients and staff. The implications of Internet of Things data collection for drug management are enormous as they help improve medication adherence, monitor the effects of treatment, and prevent theft during shipping, as well as at the warehouse.
- Manufacturing. IoT sensors are used to ensure workplace safety (measure the number of contaminants in the air), create a favorable environment for the peak performance of factory equipment, monitor worker productivity and integrate big data performance monitoring solutions for predictive analytics and maintenance.
- Agriculture. Smart solutions are used to monitor farming sites in real-time, forecast the likelihood of natural disasters and their impact on crops. The influx of relevant sensor data helps design efficient plant treatment, monitor water usage, and reduce the amount of workforce needed to manage the site. IoT data helps farmers monitor and ensure the well-being of livestock as well.
- Energy. IoT data helps homes, offices, shopping malls, and public institutions reduce energy consumption. By tracking the amount of electricity spent by the property, facility managers become more aware of potential ways to reduce energy consumption. Processing sensor data lies at the core of smart light and temperature trackers, intelligent energy managers, and connected devices.
- Smart homes. In the last five years, the smart home market has exploded. Smart thermostats have become a commonplace item for households — these tools heavily rely on data, captured by temperature sensors. Security systems, smart plugs, and other appliances all use IoT for data collection to ensure energy efficiency, as well as in-house safety.
- Transportation. Aside from autonomous vehicles, there’s no lack of smaller-scale connected applications. Traffic congestion managers, virtual parking assistants, fleet management tools, and fuel consumption monitoring devices are all sensor data collection examples.
Things to Consider When Collecting IoT Data
Other than focusing on building responsive and easy-to-use IoT systems, tech teams need to create secure and reliable data collection and processing practices inside the system. The reliability and scalability of the solution all stem from the practices business owners use to capture, sort through, store, and relay IoT data.
Capturing data is the first layer of IoT application architecture — teams should ensure that a device is capturing relevant real-time information. In case of a sensor malfunction or processing errors, the end-user is likely to get false data. Considering the scale and industries IoT devices are deployed in — banking, healthcare, transportation — the impact of poor sensor data collection practices could be staggering, leading to financial losses or accidents.
Legal compliance is another point teams should keep in mind when designing data collection practices. Developers need to integrate security into all layers of IoT applications and demand consent from device users when capturing data to avoid GDPR and other legislative fines. To make sense of all the data sensors collect, tech teams can also benefit from using metadata and assign meta-tags to existing IoT data. This way, IoT engineers will facilitate the process of sorting through, monitoring, and storing different types of data.
Data Security in IoT
NETSCOUT’s Threat Intelligence Report released overwhelming statistics recently — it takes up to five minutes for an IoT device to get hacked once it’s connected to the Internet. These findings are proof of both of the vulnerabilities of connected systems and hacker’s growing desire to get ahold of IoT data for spamming, identity theft, blackmailing, and other purposes. What can tech teams do to build tamper-proof connected systems? Here are the practices IoT developers implement to create an impenetrable framework for data collection and IoT device management.
1. Building tamper-resistant hardware
Since IoT sensors and other devices often operate 24/7, it’s impossible to have constant surveillance over them. To make sure there’s no way for third parties to access the hardware, business managers should consider keeping IoT devices in an isolated space to have a better idea of who can access them. Other ways to improve the security of endpoints are:
- Automatically disabling the battery of a device when someone tampers with it;
- Using port locks to restrict access to USB, camera, and Ethernet ports;
- Creating strong boot passwords;
- Tracking access to serial ports, UDP/TCP ports;
- Creating tamper-evident packaging — a device owner will know right away if the hardware has been opened before it arrived.
2. Running dynamic testing on IoT devices
This way, a tech team will expose a wide range of defects and vulnerabilities both on hardware and software levels. The static analysis doesn’t offer that much insight into processor and memory vulnerabilities. Being able to examine the behavior of the new code when it interacts with old processors is an additional step to validate the reliability of the system before bringing it to the market.
3. Have set-in-stone data disposal algorithms
A tech team should account for what happens to IoT data when a user throws a smart device away. Failing to discard personal information can lead to its misuse and expose user’s sensitive financial, location, or health-related data. The most common data disposal practice is ‘discard, recycle, or destroy’ — in short, DRD.
IoT device manufacturers encourage users to contact the company before getting rid of a smart appliance so that a professional team can handle data deletion. Device manufacturers could allow users to enforce individual DRD policies, deciding whether authentication and personally identifiable information should be stored on a device or on a remote server. Here, the lack of tech skills among smart device users is an issue to tackle, as most would struggle to understand the full complexity of IoT password storage.
IoT Data Collection Technology and Process
To get a better idea of how IoT based data collection works, let’s examine the moving parts of any connected system. IoT application architectures are typically complex — however, most projects consist of standard components.
Device Layer
A range of devices that communicate with one another is the primary layer of IoT architecture. Here are the most widely used examples of IoT data collection technology:
- Sensors that track motion, temperature, heart rate, and other variables;
- Actuators;
- ZigBee devices;
- Bluetooth and BLE devices;
- Low-power-radio-based devices.
All IoT devices have an identity that falls into one of the following categories:
- A built-in unique identifier (or UUID) placed inside of a device, like a chip;
- An identifier that relies on radio IoT data collection systems — Wi-Fi MAC, Bluetooth, etc.;
- An identifier located inside the system’s non-volatile memory (EEPROM);
- A Refresh/Bearer token.

Communication Layer
This part of the architecture allows devices to communicate with each other and exchange data. The communication layer consists of protocols, among which the following ones:
- HTTP/HTTPS — a basic text-based protocol supported even by low-end 8-bit devices.
- MQTT — a protocol, designed to handle embedded systems and optimized to support IoT. It is known for a wide community of followers, as well as a robust asset library.
- CoAP — based on HTTP semantics, CoAP scores higher in terms of a footprint. Compared to MQTT, the protocol is harder to connect to firewalls and has poorer library support.
IT Edge Layer
This layer is often considered the application’s command station as it brokers communications. In an IoT application, it carries out the following functions:
- Device management;
- Ensuring processing security;
- Aggregating and replicating data;
- Routing data to/from the cloud;
- Priority messaging;
- Processing images, audio, and other types of data at the edge.
The edge helps ensure that most data processing is happening off the connected device in a dedicated environment. The layer is used to support a wide network of devices that have the little-to-no processing power of their own but will supply the system with high data volumes.
Event processing layer
After IoT data is collected, an application needs to process and store it — this happens in the event processing layer of the system. In this layer, multiple operations are handled:
- Cleansing the data;
- Structuring gathered insights;
- Storing the information inside a database;
- Adding metadata to IoT data.
There are several ways to build this part of the system — you can either design a database-powered server-side application (a JAX RS tool, for instance), use IoT cloud services to process and store IoT data, or support real-time event processing from IoT devices.
Client communication layer
In this layer of the IoT architecture, all collected data is transferred from a device-oriented to a user-oriented system. To relay data from IoT devices to end-users, a tech team needs to build front-ends that interact with databases and the back-end. To make sure that IoT data can interact with outside systems, developers employ machine-to-machine APIs. The most common way to relay IoT insights to an end-user is via web or mobile applications.

Challenges in IoT Data Collection
The growing number of connected devices means having to deal with higher data volumes — as a result, application architectures will get more complex and demanding maintenance-wise. Before committing to an IoT project, a business owner should be aware of risks that are likely to manifest in the long run. Here are the main challenges with IoT data collection are facing when it comes to collecting and processing IoT data:
- Huge data volumes to sort through. Data preparation is one of the most time-consuming tasks for any software or web project — tech teams need to sort through terabytes of available information. As there’s a higher influx of data, current data preparation strategies might not be able to keep up. Thus, business managers need to look for ways to optimize data storage and automate preparation processes.
- Compatibility with existing systems. Poor IoT data interoperability is another issue tech teams need to resolve proactively. As of now, most tools are not equipped to handle sensor- and other Internet-of-Things-based information. Thus, business teams will struggle to find suitable repositories to move IoT data.
- Security. This is an inevitable concern when it comes to IoT data capturing, processing, and storage. The insights sensors and other devices collect are oftentimes sensitive — health-related, location, private space data. The impact of misuses could be staggering and jeopardize the safety of entire organizations and communities.
- Streamlining challenges. As they aim to get a real-time stream of relevant IoT data, business managers should strive for consistency. However, ensuring 24/7 error-free communication between devices, information processing inside a gateway, and putting the insights out in a comprehensive form is an expensive and complex project. To build a functioning IoT system, tech teams need to find a way to process data on the fly, correlate real-time events with one another, and store them securely in the operational database.
Data Collection Solution at Digiteum
The proliferation of IoT devices and the wide range of opportunities they offer in all sectors of life means that business owners should be more aware of how such systems operate and the risks collecting Internet of Things data brings forth.
The good news is, by implementing edge computing, machine learning, and other advanced technologies, tech teams should be able to find affordable and efficient ways to sort through data, process the most relevant insights, store and relay them to consumers successfully.
If you are looking for a reliable big data development company to build a reliable and scalable data pipeline, set up and support data infrastructure, and design and implement interactive dashboards and monitoring tools for your IoT project, contact Digiteum. Our developers are experienced in building big data solutions for connected systems in healthcare, energy, smart homes, and other major industries. Contact us to discuss your project.